RIASC RESEARCH AREAS
Big Data and Machine Learning in Cybersecurity
Trustworthy systems
- User-centric Privacy and Security
- Dependable and Secure Systems
- Defense against Emerging Threats
- Auditing, Forensics, and Certification of Secure Systems
Security in cyber-physical systems
- Reliability of Critical Infraestructures
- Robotics, Sensor Networks, Surveillance, and Biometrics
- Linear Attack Policies. Test and Dissuasion
Hardware-based security
Applied cryptography
- Fast algorithms of Code/Decode of Data Flow
- Multichannel Cryptography
- Exchange Protocols of Multipart Keys
- Homomorphic Coding
Network analysis
- Network control
- Topoi in networks
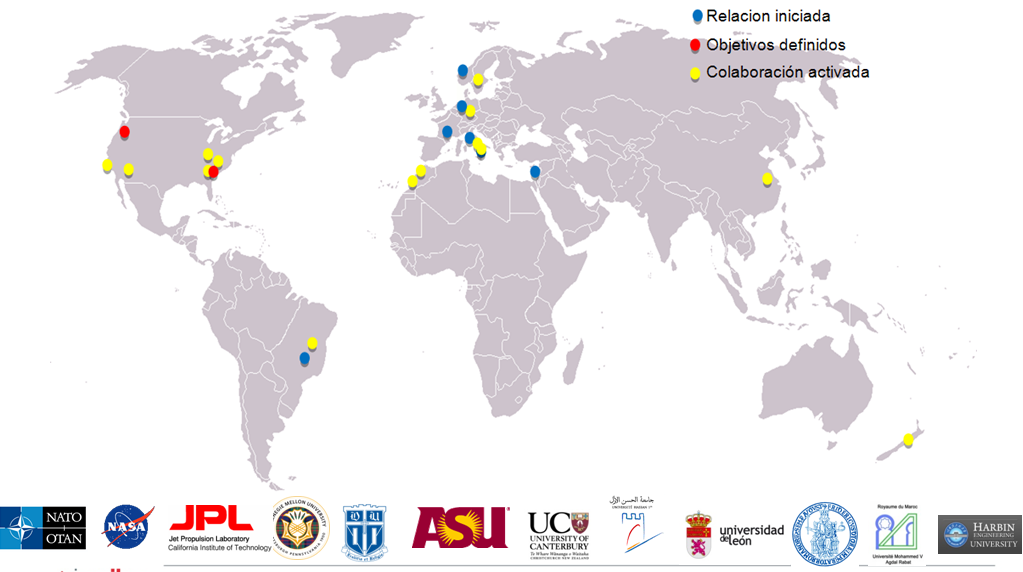
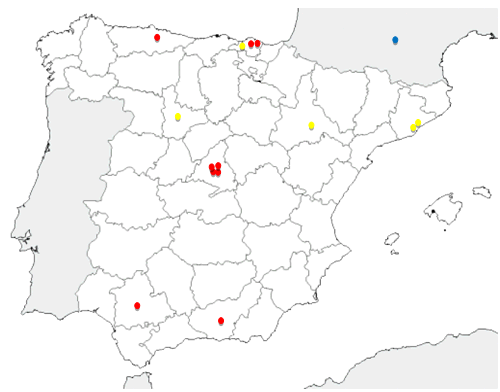
RELATIONS ESTABLISHED
International Relations
National Relations
RESEARCH PROJECTS
Intelligence Model Project
- Targets:Design of the INCIBE Intelligence Model; development of exploratory and diagnostic analysis of security events data, as well as preparation, advanced analysis and categorization of their reliability.
MITHRA Project
- Targets:Design and develop MITHRA, an intelligent system , distributed with minimal human intervention, based on artificial intelligence and machine learning for response to attacks and security incidents based on Software Defined Networks.
RULE Project (Remote Unit for Lightweight Exploration)
- Targets:Tasks of research and development of sensing , navigation algorithms and vision of an autonomous mobile robot and remote control capability for use in the forensic field in hostile environments for human life.
SAFNC Project (Spectral Anti Forensics for Networks)
- Targets:Network identification by the characteristics of the graph. Control of the characteristics of a graph from one node of the graph : It is theoretically possible and is a new topic . Implementation of supervised concealment tools and automatic
- Motivation: You can audit the activities of a network (communications, social network ) based on the flow of communication between its nodes. an automatic method is proposed to hide the network structure and prevent the most common types of statistical audit (cluster analysis, principal component analysis, clique formation, big component).
Vulnerabilities, Threats and Countermeasures Modeling in NFC and mobile devices
- Target of basic research: Analysis, classification and parameterization of malicious software..
- Transferable objectives: Analyze communication protocol NFC , looking for possible attack vectors and exploit them. Audit of banking and Public Administration . Other vectors exploitation and malicious software with NFC capability.
Proyect Cloud cybersecurity tools: Homomorphic Cryptography and Optimal security-based placement
- Targets: It aims to develop purely algebraic algorithms and current results in specific protocols. Homomorphic cryptography techniques . Protocols and coding applications texts. Idem images. Prepare a report on cryptographic techniques for cloud . In particular develop optimization algorithms that take into account not only performance and reliability , but also security when deploying cloud services.
- Motivation: Two lines of research of direct application in cloud services. The homomorphic cryptography allows, among many other applications, to work with encrypted data securely Cloud. It is also necessary to ensure optimum distribution of cloud services in the data center.
REPTill. RFID Enabled and Private Till
- Target of basic research: Security (and privacy) in cyber- physical systems.
- Transferable objectives: Construction of prototype lock security / privacy means of payment. Validation studies.
User-centric privacy for mobile environments project
- Targets: Models , standards and tools aimed at ensuring the privacy of end users in mobile environments including smartphones , tablets and emerging technologies such as the Internet of things.
Industrial Infrastructure Cybersecurity and SCADA systems reviews
- Target of basic research: Cybersecurity in industrial environments.
- Transferable objectives: SCADAS.
RESEARCH GROUPS
Grupo CIBERSEGURIDAD. APLICACIONES, FUNDAMENTOS Y EDUCACIÓN (CAFE)
Interdisciplinary research group focusing on a variety of Cybersecurity topics: Cryptography; Codes; Dynamical Systems; Graphs and Networks; Data Analysis; Analysis of Experiments; Secure Software Development; SDN; Surveillance; Computer Vision; Malware Analysis; Security; Security Incidents; Cybersecurity Education; Teaching and Learning.
Grupo de investigación de seguridad GISSiM
The security research group GISSiM (short for "Security Research Group Mobile Systems") directed by Vicente Olivera Matellan, is a research group at the University of León working on security in mobile systems. The group was established in 2012 and is currently working with INCIBE to analyze and improve security in iOS environments.
The group studies security issues in different environments. One of the main issues is to ensure, auditing and analysis applications iOS system and iOS.
GISSIN and the Universidad de León group are distributing this information as academic dissemination of their research results without any implication or claim for the safety of these applications.
The main page with more information about GISSiM can be found here: http://seguridad.unileon.es
Grupo de ROBÓTICA
They are a group of researchers (faculty and students) interested in creating autonomous behaviour for mobile robots.






